Background
Important text messages within, and between two or more nations, their armed forces, embassies, and so on are being encrypted(so only the sender, and the receiver can read the plain text, for others, it is an obfuscated, unintelligible text) for centuries. This practice was getting increasingly complex/secure after the WW-I. Enigma was a cipher machine used during the interwar and WW-II by the German military. In this series, I will try to present whatever I have learned recently about Enigma, it’s usage, and it’s cryptanalysis by the Allies.
Context
This post will focus on the origins of Enigma, and bird’s eye view of it’s functioning. The subsequent posts would have more explanations, deep-dives, and progress towards the cryptography and cryptanalysis, and last but not the least – timeline.
Origins
Contrary to the popular belief, the Enigma was neither created by any military organization nor was the military or government its initial buyers. My lame guess is that due to the restrictions imposed on Germany after the WW-II, they might have brought in Enigma as a commercial product. Enigma’s primary objective was to securely transmit banking, commercial information. Assuming this is true, it is another example of how a machine, an idea intended for a particular use case ends up being used for several more e.g.: The Jeep.
Early Enigma Machine
Take a look at the below images as well to understand a bit about the various parts. Note that these images do NOT correspond to the above, older Enigma machine but to later, advanced machines e.g.: the above machine didn’t have a plugboard, it was introduced in 1930.


| Number | Component | Description |
| 1 | Keyboard | The plain-text message would be typed using this. |
| 2 | Lamp Panel | An alphabet would be lit on this panel for each plain-text alphabet typed on the keyboard e.g.: For ‘A’ typed on keyboard, ‘E’ would be lit on the panel. |
| 3 | Rotor Settings Viewer | View the current rotor settings. |
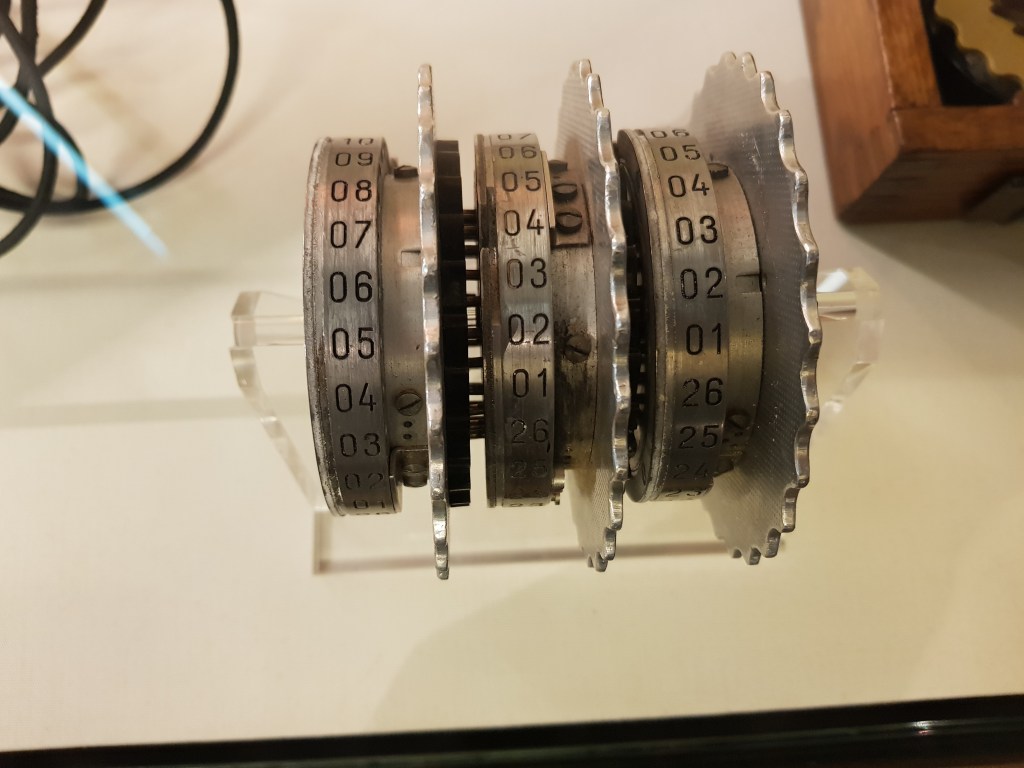
| 4 | Rotor | Each plain text alphabet would electrically pass through each rotor. |
| 5 | Power Selection Switch | |
| 6 | Contacts for external power source | |
| 7 | Spring for letter ring | |
| 8 | Letter rings | |
| 9 | Lever | |
| 10 | Springs for anti-glare screen | |
| 11 | Reflector | After an alphabet was passed through each rotor, it was finally passed through the reflector and sent to the lamp panel. |
| 12 | Cover screws | |
| 13 | Guide pin | |
| 14 | Battery housing | |
| 15 | Plugboard | Not present in the K model or pre-1930 Enigma machines. |
| 16 | Rotor cover |
Operation
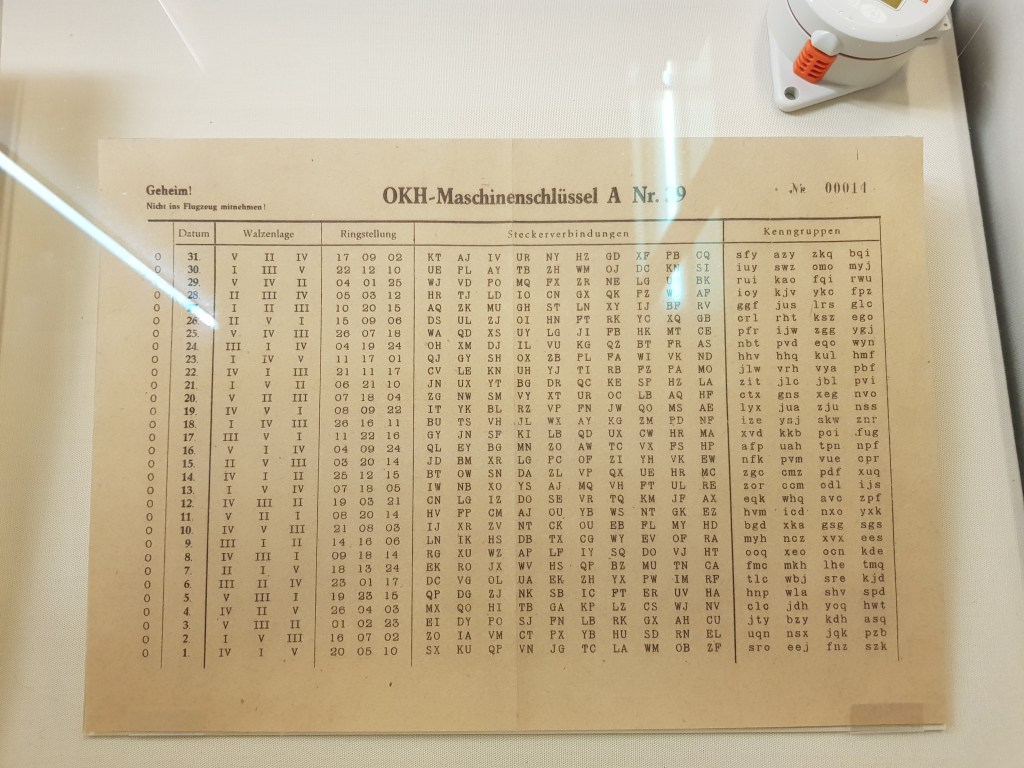
- Every month, all the German military and diplomatic units would get a manual of keys(check photos at end of this list) to be used for encryption/decryption.
- An operator(sender) would first open the machine(check image ‘Open Enigma’ in the previous section), take out the three(or whatever be the number) rotors out along with the spindle. Each rotor had a printed/assigned number(check photos at end of this list).
- He would then set the three rotors back on the spindle, left to right, in a pre-decided order e.g.: rotor-3 goes left, rotor-1 goes in the middle, and the rotor-2 goes in the right.
- Once the rotors were arranged, the next step was to set pins on the each rotor.
- Now, the rotors were placed back and the machine’s lid was closed. Encryption for the rest of the day was now set.
- The power selection switch was now moved to left to start the machine.
- The operator would start typing a message to be sent on the keyboard. Another person would be observing the sequence of the letters lit on the lamp board, and note the same.
- The encrypted sequence was now ready on a notepad.
- A radio operator would now first transmit a message preamble, followed by the encrypted message. To be clear, this transmission was sent using the Morse code.
- The receiving side must have an Enigma machine with rotor settings identical to the sender’s. The operator would then simply type the encrypted message, and the lamp board would show the decrypted/plain-text message. The Enigma machine, thus, was used for both encryption and decryption.